It seems like
T-Mobile is embroiled in a new controversy at least once every few weeks of late, but while
some attempts to scam customers are relatively easy to avoid and
certain fees are not that big of a deal in the grand scheme of things, other security issues are both incredibly serious and virtually unavoidable.
Known primarily for its cheap plans and unbeatable device promotions not that long ago, the “Un-carrier” has made far too many
headlines involving the words “data breach” over
the last few years. Yet another such incident may have taken place at some point in the recent past, exposing the phone numbers of company employees to bad actors who are now attempting to cash in on this data.
What’s that and how scary is it?
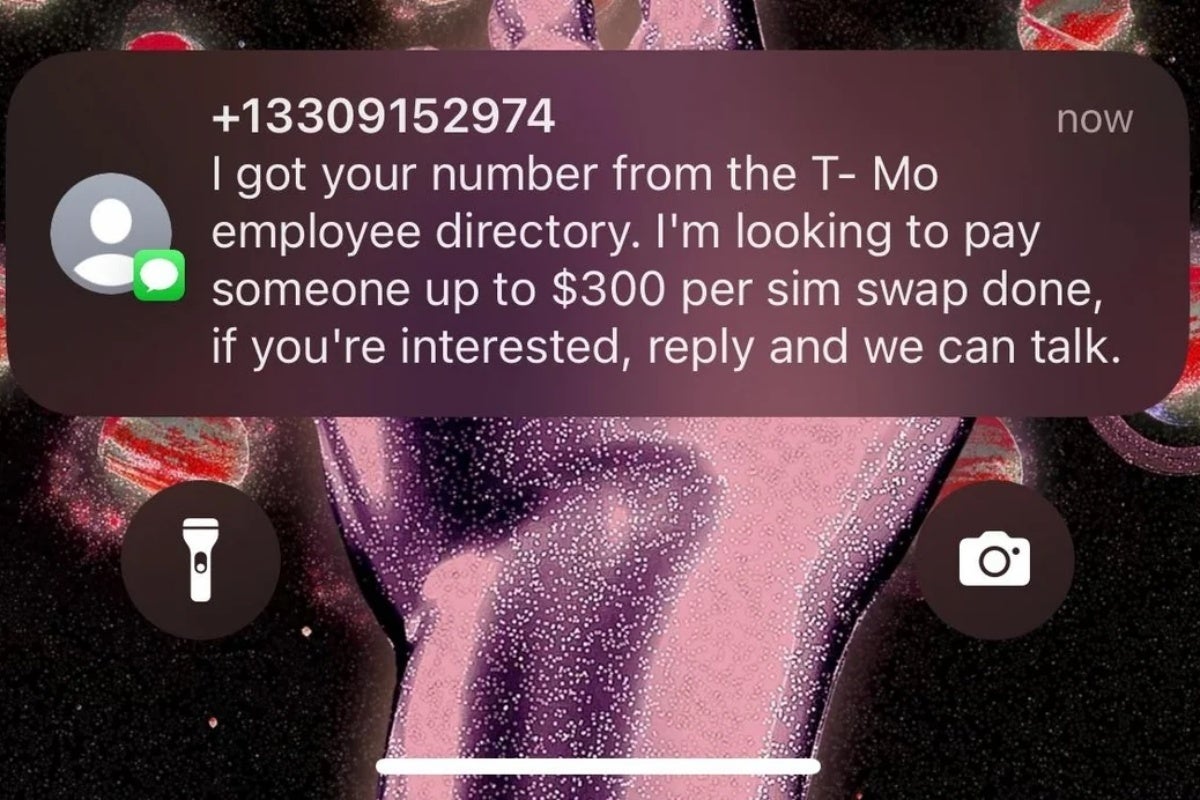
SIM swaps, for those pure souls who are unaware, remain probably the biggest security danger faced by mobile users around the world, far too frequently ending in financial losses amounting to way more than $300. While these types of attacks don’t always have the same cause or origin point, bribing a carrier’s employees to supply sensitive user information or even perform unauthorized SIM number changes themselves tends to work like a charm… in an obviously bad way.
Of course, a hacker first needs to obtain an employee’s contact information to try to carry out such an insidious action, which has clearly already happened here. What’s unclear is
howT-Mobile allowed that to take place,
when this operation occurred, and
if it’s in any way connected to any previously known data breaches. If the answer to that latter question is no, then it’s obvious that Magenta is facing a new security “situation.”
Need a quick $300? Try to do literally anything besides accepting this offer!
Worse yet, this could always devolve into a much bigger debacle if any employees contacted by these bad actors decide to accept the SIM swap offer and deliver the customer data required for this type of fraud in exchange for a cool 300 bucks per account takeover.
You are of course not advised to ever attempt that if you’re in a position to help make it happen, both because you can cause a lot of people a lot of harm and because you will almost certainly face legal consequences.
What can users do to stay safe?
SIM swaps are no joke in the eyes of the law, and should definitely not be treated lightly by mobile phone users either. The good news is you can stay protected from any such incidents if you follow a few basic security principles.
Firstly, you need to understand that two-factor authentication and two-step verification are not infallible methods to keep your private data secure. They are useful and should clearly be enabled wherever possible, but don’t rely very heavily on SMS-based verification.
That’s actually the easiest way for bad actors to take over your accounts to a lot of online services, including banking and cryptocurrency apps. Secondly, if you do choose to trust this method of authentication, be sure to at least look for typical red flags in the phone numbers and links sent to you via text message. Only access trusted websites from your phone and double, triple, or quadruple-check numbers claiming to be T-Mobile support or customer care.
Last but certainly not least, you should know that T-Mo has very specific
SIM protection tools in place… that
you may need to activate by diving into the “Privacy and notifications” section of your account settings. Unfortunately, those are not 100 percent impenetrable either, which is why the “Un-carrier” has to stop letting the personal information of its employees and customers end up in the wrong hands again and again.