The Trojan’s final payload will record keystrokes made by a device user in order to capture passwords. It also employs overlay attacks that trick users into thinking that they are communicating with a legit app only to interact with a malicious overlay. The attackers hope that the user types in login credentials or, even better, a credit card number, the card’s expiration date, and security code. The Trojan also uses VNC (Virtual Network Computing), a remote screen-sharing technology that can use malicious software to capture screenshots and send them to a remote server.
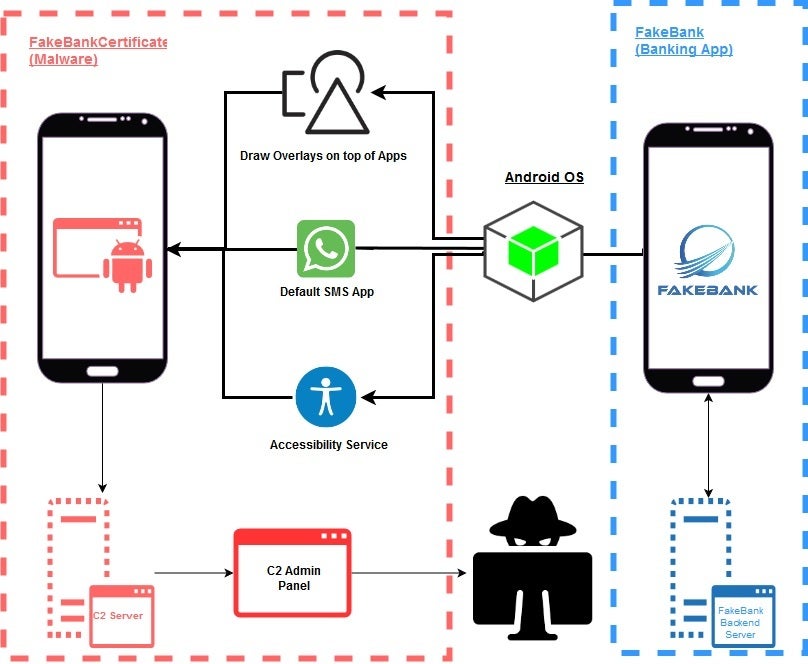
Chart showing how an overlay attack works. | Image credit-IKARUS security software
Cyble Research says that the Cerberus Banking Trojan is a good example of how malware can be repurposed and can continue to be a dangerous threat years after it originally debuted. Cerberus was first spotted in 2019 and Cyble first thought that it had spotted a new malware variant but analysis revealed that the code being used was similar to code used in the past by Cerberus. The research firm says that attacks are ongoing.
The attackers are looking for users to make a mistake since the malware disguises itself as legitimate banking or authentication apps and uses Google Play and Chrome icons. When it first hit the scene in 2019, the Trojan was used to help commit financial fraud. The current version of the malware uses a multi-stage dropper that delivers its payload in steps and can bypass restricted settings. If the primary server is unavailable, it can choose to communicate with Command and Control (C&C) servers.
The security research firm also makes a big suggestion, one that you should always follow. Never click on suspicious links sent to your phone via text or email.
