T-Mobile told
Beeping Computer that it was not hacked nor was any source code stolen even though stolen data from the wireless provider had been offered for sale by a “threat actor.” In a statement, the nation’s second-largest wireless provider said, “T-Mobile systems have not been compromised. We are actively investigating a claim of an issue at a third-party service provider. We have no indication that
T-Mobile customer data or source code was included and can confirm that the bad actor’s claim that
T-Mobile‘s infrastructure was accessed is false.”
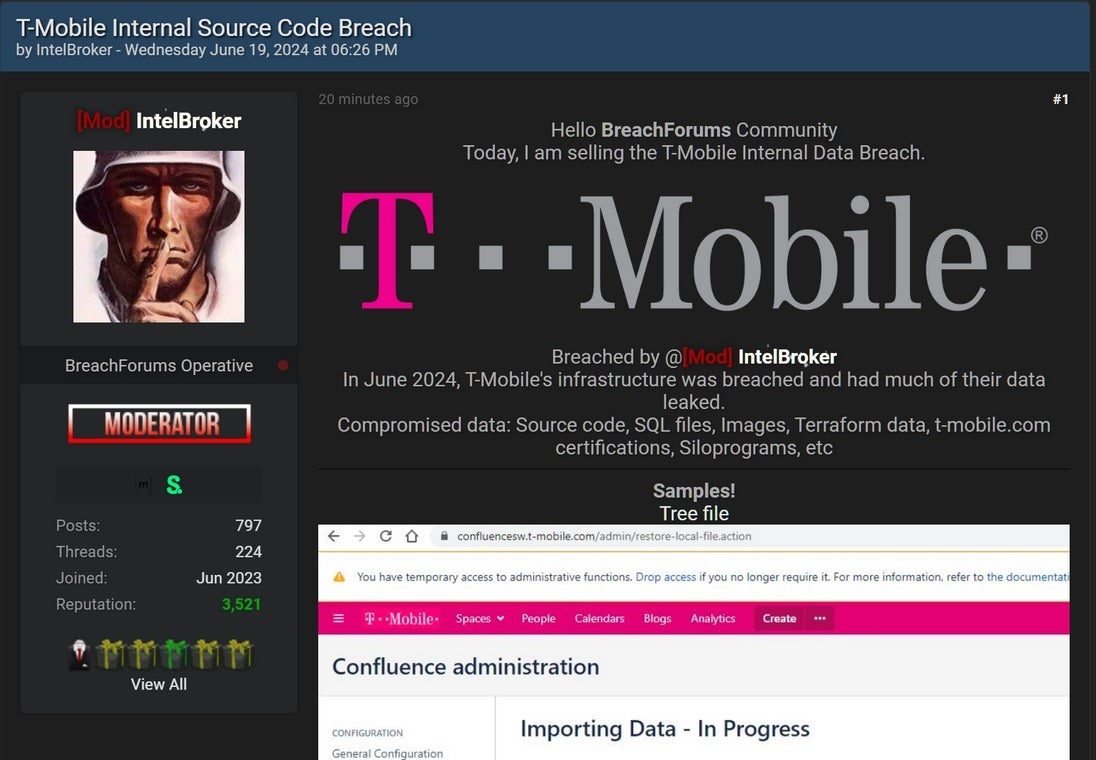
The “threat actor,” who is known as IntelBroker and is said to be connected to several data breaches, claims that he was responsible for a data breach attack against
T-Mobile that he said took place this month and resulted in stolen source code. To prove that the data he obtained was legitimate and from a recent breach, IntelBroker published several screenshots that revealed access with administrative privileges to a Confluence server and the company’s internal Slack channels for developers.
Threat actor IntelBroker claims to have breached T-Mobile’s infrastructure this month. Image credit-Bleeping Computer
It’s possible that Common Vulnerabilities and Exposures (CVE) listing CVE-2024-1597 was exploited to obtain the data since this vulnerability affects Confluence Data Center and Server and according to Bleeping Computer, has a severity score of 9.8 out of 10. But at this point, it is not clear whether the aforementioned third-party vendor was breached using this vulnerability.
The data that IntelBroker says that he is selling includes “Source code, SQL files, Images, Terraform data, t-mobile.com certifications, Siloprograms.” A source told Bleeping Computer that the data being sold “is actually older screenshots of T-Mobile‘s infrastructure posted to a third-party vendor’s servers, where it was stolen.” This would dovetail with T-Mobile‘s statement that it is “actively investigating a claim of an issue at a third-party service provider.”
Source Link Website